Technologies
January 2023
Connectivity has become the new norm for products, and medical products are no exception. This trend has introduced new challenges in terms of data security. Therefore, cyber security has become a cornerstone of today’s product development and must be extended throughout the full development lifecycle. Both the methodology and mindset must be adapted. Helbling addresses each of these in its development process and has continuously improved it over recent years.
In light of the connectivity trend, data security is an increasingly important factor in product development. This applies to all product areas, especially medical products with personal health information. It is always important to protect sensitive data and to comply with complex regulations. In this context, gaining and retaining the comprehensive trust of customers becomes an elementary goal. At Helbling, security is integrated throughout development. In recent years, there has been a lot of work on establishing a special mindset among developers and on a template for assessing cyber security risks, among other things.
A recent project serves as an example: Helbling has developed an accessory that can be physically connected to an already existing medical product. The accessory allows data to be transferred to a remote site for data analytics. Furthermore, the medical device can also be controlled remotely with the appropriate access rights. Access control and data protection based on cryptography was at the heart of development, including secure end-to-end design.
Developer mindset
In traditional security models, the main focus of protection is on security measures at the perimeter of the network, such as firewalls. With traditional security models, all entities are considered trustworthy once they have been connected and authenticated. But since attackers can use valid identities to bypass network controls (i.e., gained by social engineering activities), the traditional approach is no longer sufficient. Instead, nothing should be assumed to be trustworthy without recent proof; therefore, a change of mindset is required towards zero-trust.
Zero-trust must start with the mindset of people, and this includes the engineers at Helbling: Each employee must continuously pass awareness training and is challenged every now and then with social engineering activities, e.g., crafted phishing mails.
Integration of security into the development process includes automated security checks in the supply chain and in all the products. Developers get early feedback if risky code (e.g., by third party dependencies) is introduced to the product or the infrastructure. Established quality gates to reject code or dependencies with vulnerabilities are an integral part of the development process. Findings are then fixed before bad code or vulnerabilities become part of the product.
Development methods
But people are not the only identities within the network, the same applies to devices too. In this regard, it is crucial to focus on making device identities resistant to hacking attempts, e.g., by leveraging hardware security modules and using authentication on interfaces.
Helbling has established a template for assessing cyber security risks based on the Microsoft model STRIDE in compliance with the standards inspired by the Failure Modes and Effects Analysis FMEA, allowing structured, systematic identification and rating of cyber security risks (assets, attack surface) and tracking of measures during development.
Medical product monitor
The methods described above have been used exemplarily in the development of an accessory for a medical device for one of our customers.
The purpose of the accessory is to monitor the medical device usage and write usage logs without an impact on the intended use and performance of the medical device. In the beginning, experts analyze the system architecture and identify interfaces, information elements (data), and hardware. The medical product monitor added two new critical interfaces to the medical product: The first interface is used on site by medical staff to retrieve log information from the devices. The second interface is used to prepare, configure, and control the monitor.
After the identification of assets, a potential threat analysis is performed by applying the threat modeling systematic, including vulnerability scores to prioritize the threats. The method is similar to a FMEA.
The last step is deciding what to do: Measures are defined and implemented depending on priority. During verification, the implemented measures are verified, and penetration tests are also executed during product validation.
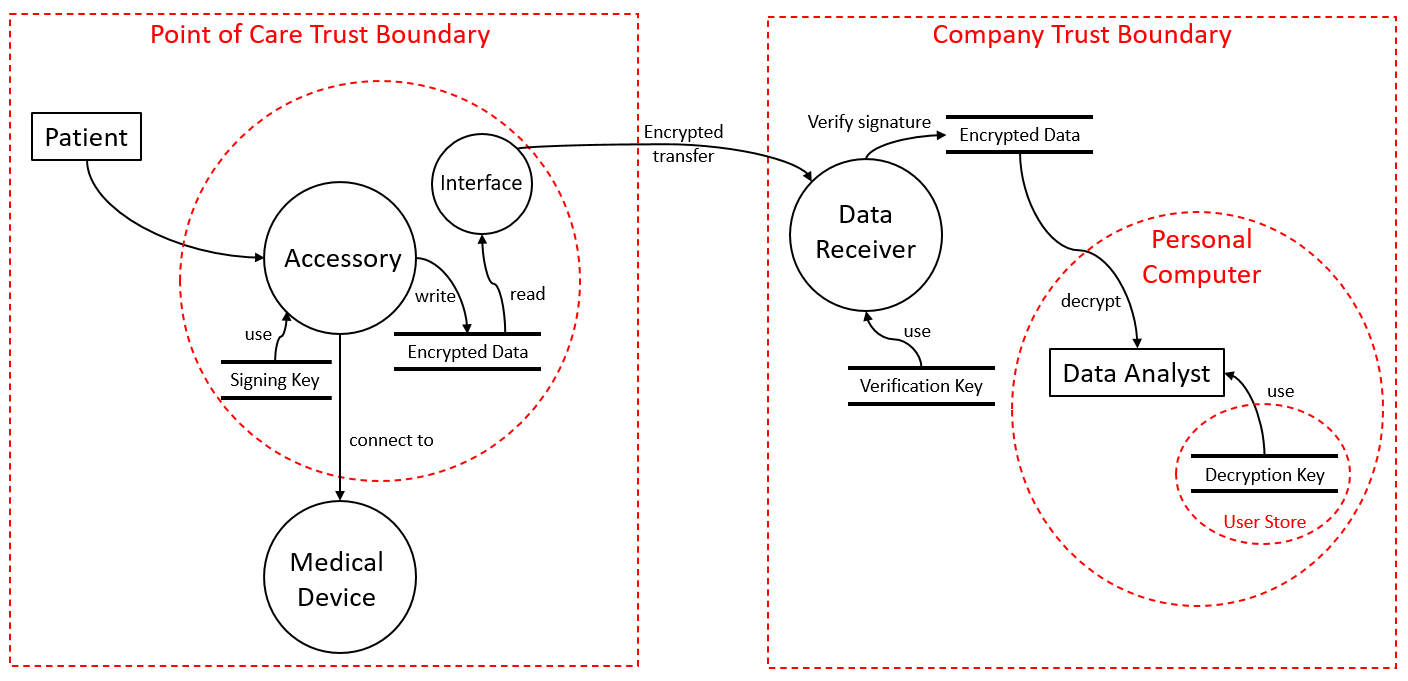
Applying the threat modeling to the monitor led to the implementation of various cyber security measures, such as to detect any manipulation of the recorded data, whether by a malicious actor, a bug in the device, or by the patient. The monitor makes heavy use of cryptographic operations: To preserve confidentiality, data is encrypted as soon as it is recorded, meaning that it is never saved in clear text. To ensure integrity and authenticity, data is signed using individual cryptographic certificates per monitor. Additionally, secure elements have been integrated into the electronics design. These modules ensure that the sensitive keys cannot be read out or manipulated from outside the system using only minimal space on the printed circuit board.
Access to the device and decryption of data is done using several security levels. While a healthcare provider can collect the data, only dedicated employees of the medical device manufacturer are able to decrypt the data. Data always remains encrypted in transfer and at rest. Another key measure against breaches is the ability to update the monitor’s software out in the field. Again, integrity and authenticity are ensured by certificates. The device manufacturer signs the new software based on a certificate the accessory has stored in its secure element.
Summary: Integrating cyber security into product development needs the correct mindset and methodology
Helbling has established the right mindset and methods for integrating cyber security as an essential cornerstone in the development of connected products. Using a risk-based approach minimizes the overhead of cyber security while achieving the right level of security.
Authors: Torben Rühl, Frederic de Simoni, Urs Anliker
Main Image: Pexels





